IT Risk Management Process for ITIL® v3 & ITSM Environments


Dealing with risk is an important part of deploying new services in an IT service management (ITSM) environment. IT risk can occur in several areas during service delivery, including operational, legal, and financial risks.
Besides minimizing problems in service delivery, many government and regulatory agencies also routinely review organizational risk management policies and responses. Implementing and controlling risk in an ITSM environment is not only smart business; it can also be a regulatory requirement.
IT risk management is a continuous process that has its own lifecycle. Although experts differ on what steps are included in the process, a simple IT risk management process usually includes the elements shown in figure 1.

Let’s break these steps down and look at how each step manages risk in an ITSM environment inside an ITIL® v3 framework. (Looking for ITIL 4? Check out our ITIL 4 Guide.)
Specific organizational risks should be identified whenever an item will be added to the service catalogue or when an existing service catalogue item is going to be modified. Risk identification ideally occurs in the Service Design phase or the Continual Service Improvement phase of the ITIL framework, where new services are defined and committed to.
There are several ways to identify risks in rolling out a new service catalogue feature, including:
Risk identification should always include a description of the risk and the potential impact that will occur if the risk is realized. Potential impacts should be scored as to whether each risk carries a potential high, medium, or low impact on the business. Scoring impacts will help you decide what (if any) resources, you should allocate to addressing each risk.
(Try the impact, urgency, prioritization matrix.)
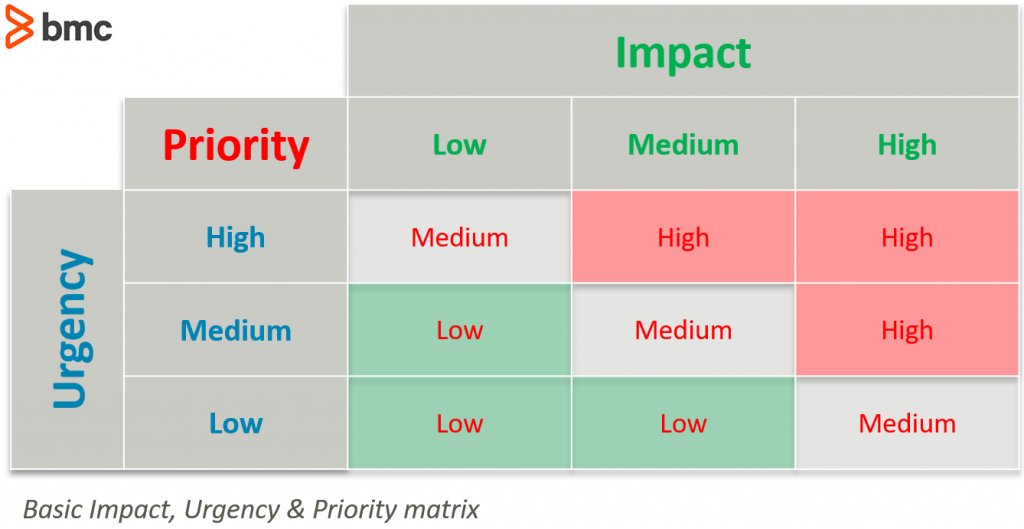
Probability of risk occurring and prioritizing risks: It’s important to determine the probability that a risk will occur as well as the importance of each risk. Probabilities can also be classified in simple terms such as a low, medium, or high probability.
Take, for example, a new service to provision cell phones where you may identify the following risks and their probabilities of occurring:
Determining the probability of each risk occurring helps prioritize which risks you’ll need to develop response plans for (see next section) and the order in which each response plan should be developed.
How will your service desk and IT department respond if any of the identified risks occur? IT departments can generally create a response plan for dealing with risks by using one of the following techniques.
It’s important to monitor and identify risk triggers that activate a response. The trigger for cell phone issues would probably be a user support call. For operational support, organizations can install performance and availability monitoring software such as those in the BMC Helix and TrueSight Operations Management portfolios. Monitoring software can automatically alert on-call IT responders when issues are detected.
When new risks are identified, they should be evaluated in the context of the established management process and reflected in an updated risk management plan. In the ITIL framework, improvement is implemented under the Continual Service Improvement practice of the ITIL Service Lifecycle.
There’s one other step in the IT risk management process that’s implied but not listed here: documentation. It’s important to document realized risks and their responses as they occur for two reasons: