OSI Model: The 7 Layers of Network Architecture


The OSI (Open Systems Interconnection) Model describes how networked systems communicate. It is a theoretical framework for mapping how applications and devices link and send data over a web of connections.
The OSI Model is called a “reference model” because it is rarely used in practical applications. Instead, it is most helpful in describing network protocols and services. The OSI Model is most often used to understand the theories behind networked communication concepts and elements. Some use it to troubleshoot problems, narrowing a potential issue to a specific layer of the model.
OSI layers are, indeed, fundamental to the OSI Model. The framework is a stack of seven layers, each performing a specific function, yet working together to transmit data from one networked device to another. The 7 layers of OSI model ensure the interoperability of different devices and technologies from various vendors.
The OSI 7 layer model illustrates how information moves from a sender to a receiver and back again. This image illustrates the 7 layers of OSI model architecture. Below, we’ll briefly describe each layer, from bottom to top.
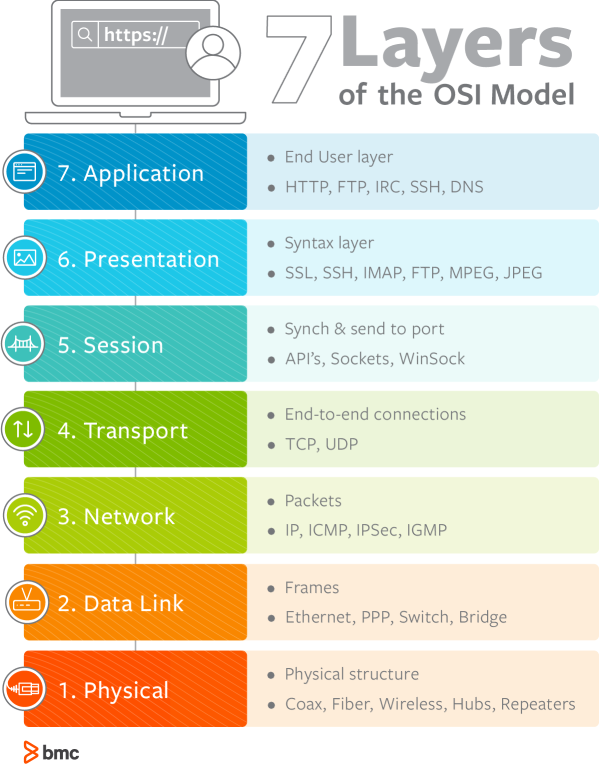
The first OSI model layer describes the physical connections between devices in a network. Electrical, optic, or electromagnetic signal data moves from device to device through the physical infrastructure defined by this layer.
The second OSI model layer describes data transmission between network devices. Data is sent in packets within a frame of special bit patterns or codes that indicate the beginning and end of each packet. These packets move through switches that route information through the physical layer from one physical location to another.
The third of the OSI layers organizes and transmits data between multiple networks. Network layer hardware includes routes, bridge routers, 3-layer switches, and protocols such as Internet (IPv4) Protocol version 4 and Internet Protocol version 6 (IPv6).
This layer routes data via the shortest or fastest physical path, working around traffic controls, congestion, broken links, service priority, and more. It handles addressing logic to distinguish between the source and destination networks. It divides data into packets to send and then reassembles them at their destination.
This layer deals with sending and delivering of complete and reliable data from one device to another through a network or between networks. Common transport layer protocols include the Transmission Control Protocol (TCP) for connection-oriented data transmission and the User Datagram Protocol (UDP) for connectionless data transmission.
Some of the essential functions in this layer include:
This OSI Model layer concerns itself with managing session links between network devices with a specific beginning and end. The essential functions include establishing a link to start the session, authenticating senders and receivers, authorizing communications between devices and apps, maintaining the session, and terminating the connection, which are the key functions.
A common session type is when an internet user visits and browses a website for a specific period.
An essential concept in this layer is synchronization, in which checkpoints during the session ensure a coordinated data flow that is free of unplanned breaks or data loss.
Data flows as packets of code, often encrypted, through networks. Presenting it in a useful format is the focus of the sixth OSI model layer. The presentation layer deals with:
To send text across a network, the characters of the alphabet convert via a character coding system, such as the American Standard Code for Information Interchange (ASCII) or Extended Binary Coded Decimal Interchange Code (EBCDIC) that is then encrypted and compressed and sent over the network. On the receiving end, the process reverses. Different kinds of data get translated into different format codes.
The top layer of the OSI 7 layer model is the application layer. It is how a user application, such as a website, browser, email, instant messaging, file transfers, or voice-over IP, interfaces with the network. Think of it as the window for accessing the network to send or display data, which can be anything from a picture of your pet cat to a database of statistics to a voice message.
It facilitates networking requests, determines resource availability, synchronizes communication, and manages application-specific networking requirements. The application layer also identifies constraints at the application level, such as those associated with authentication, privacy, quality of service, networking devices, and data syntax.
The OSI model is not widely used because of its complexity. Every OSI layer has rules and operations, which make implementation time-consuming and inefficient. The simple TCP/IP model offered advantages that the OSI Model could not match. TCP/IP was already widely used when the International Organization for Standardization (ISO) launched the OSI 7 layer model in 1984.
The OSI vs. TCP/IP debate never really gained traction in the industry. Vendors had already invested significant resources in TCP/IP products in the ten-plus years before the launch of the OSI. They had no incentive to manage the interoperability issues with the vast choices of protocols and specifications offered by the OSI model. Additionally, the creation of the OSI Model was driven by European political and economic interests that didn’t want to be dependent on technologies and equipment developed by American companies. Hence, a non-governmental organization, the International Organization for Standardization, designed the rather ponderous new model by committee.
In the OSI vs. TCP/IP debate, the original technology claimed advantages over the 7 layers of OSI model approach. Since its development in the 1970s, TCP/IP has become the proven standard that is widely used for most internet communication. Among its advantages are:
The TCP/IP architecture model has a long record of success in real-world network environments. It has served as a solid and versatile foundation for the internet, successfully addressing security, privacy, and performance-related challenges.
Continued research and development, investments, and industry-wide adoption of the OSI model could have made today’s cyber world a different ( perhaps better) place. Still, the pragmatism of the TCP/IP model has prevailed. Given its wide use and the challenges inherent in the OSI model, the ascendancy of the TCP/IP model is likely to remain for the foreseeable future.