Kerberos Authentication: What It Is & How It Works


Every time users log into a service by providing their credentials, they are potentially exposed to attacks, especially if they’re using unsafe network protocols. For instance, an attacker could use a simple packet sniffer to recover your user ID and password especially if they’re not encrypted.
What does this mean? Every time I provide my credentials to a service, should I be afraid that they could be stolen? Potentially—however, there are many precautions that we should consider when accessing a service over the internet like:
To address potential insecurity when using authentication, new safe protocols have been created and one of them is Kerberos.
Kerberos is the mythological three-headed Greek creature which is guarding the gates of underworld to prevent souls from escaping. With that as its inspiration, the Massachusetts Institute of Technology developed a protocol to protect its own projects in the late 1980s.
The idea behind Kerberos is simple: authenticating users while avoiding sending passwords over the internet.
This protocol can be easily adopted even on insecure networks as it is based on a strong cryptography and it’s developed on a client-server model. Enabling a service to use Kerberos authentication is referred to as making the service “Kerberos aware”. This is actually possible for the majority of software.
When authenticating, Kerberos uses symmetric encryption and a trusted third party which is called a Key Distribution Center (KDC).
At the moment of the authentication, Kerberos stores a specific ticket for that session on the user's machine and any Kerberos aware service will look for this ticket instead of prompting the user to authenticate through a password.
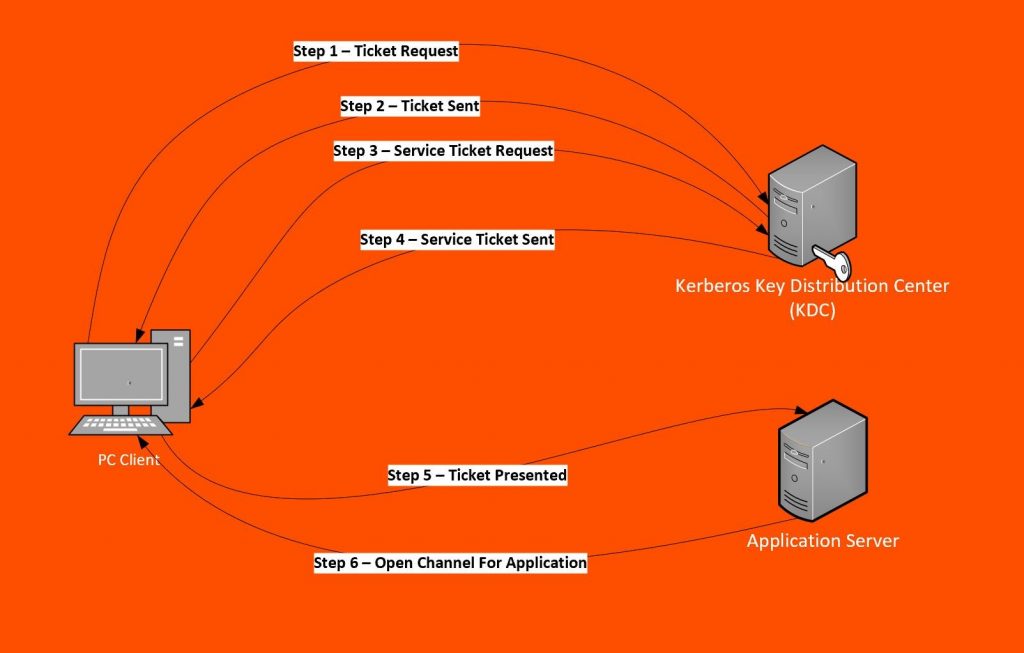 Source: BMC Software
Source: BMC Software
These are the steps in Kerberos Authentication:
Kerberos integration is also supported by Remedy Single Sign On which is the main authentication module that is used for a great number of BMC products.
In Remedy Single Sign On, it is possible to configure a Kerberos as the authentication service. In this case, Remedy Single Sign On validates the token that is sent from a client (e.g., a browser to give access to BMC Digital Workplace) together with a KDC and lets the user log into the application using her/his Windows credential.
Like many technical solutions, Kerberos has advantages as well as some weaknesses.
The principal advantages in adopting Kerberos as an authentication service are:
The weaknesses of Kerberos are:
When using Kerberos authentication in Remedy Single Sign On, you need to remember to enable Kerberos authentication for the browsers you’re using. It is not always enabled by default. Here’s how to do that for two commonly used web browsers.
For Internet Explorer:
For Firefox:
As you can see, Kerberos provides another way to authenticate that thwarts bad actors who hope to steal passwords. Even further, it can be effectively utilized with applications that are Kerberos aware. While there are some downsides, it’s another tool to make single-sign-on run smoothly while keeping passwords safe.
If you would like to utilize Kerberos with your BMC Remedy Single Sign On, please fill out our form and an expert will reach out to get you started.