Hybrid Cloud Security: Challenges and Best Practices


Hybrid cloud computing combines the benefits of private and public cloud computing: mission-critical business information can reside in secure private cloud environments on-site while cost-sensitive data and apps can run in multi-tenant cloud data centers off premise. This distribution of IT workloads is based on a tradeoff between cost, performance and dependability of a service. Hybrid cloud computing offers the opportunity to strike an optimal tradeoff—but it also faces significant security challenges.
In this article, let’s discuss some key security challenges facing the hybrid cloud as well as industry-proven security best practices to protect your hybrid cloud data centers:
One of the primary concerns that prevent cloud migration is the security of data in the cloud. While private cloud data centers may be physically located on premise, it still follows the model of cloud computing: data stored in private cloud is accessed over the private IT network infrastructure, which is potentially vulnerable to infringements, data leak, eavesdropping and man-in-the-middle attacks.
Hybrid cloud computing allows organizations to take advantage of both public and private cloud models. Benefits include reducing the risk of security threats; however, additional measures are required to manage security as the overall IT architecture becomes a complex mix of public and private cloud deployments. To ensure data security in the private cloud, follow these best practices:
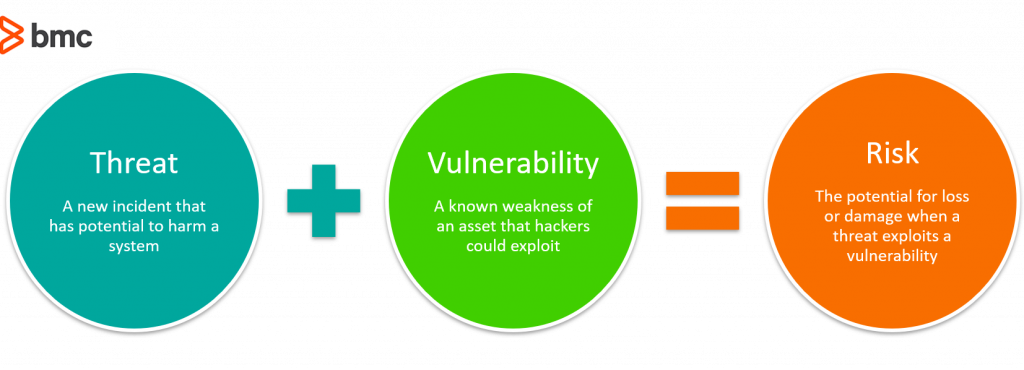
Risks facing cloud networks evolve rapidly as cybercriminals find new ways to compromise vulnerable network endpoints and communication channels. To understand cloud network behavior at any given moment, you need an accurate risk profile. This information is critical to proactively perform the necessary risk mitigation activities. It is therefore important to follow these best practices:
Cloud computing offers limited visibility and control over the IT infrastructure, as it is managed and operated by a third-party vendor. The case for an on-site private cloud would be different since the infrastructure is dedicated for use by a single customer organization and its authenticated users. The data center is often virtualized or software-defined, and these customers can maximize control over their resources. However, fine-grained visibility and control to combat hybrid cloud security solutions require in-house expertise, advanced technology solutions, and sufficient computing resources to accommodate the growing volumes of security-sensitive information and apps running within private cloud deployments in-house. In this context, the following best practices are useful:
Gartner and WSJ recently reported that human error is responsible for up to 95% of cloud breaches. These errors range from basic configuration issues and unauthorized access all the way to major architectural design flaws.
Though large cloud vendors guarantee certain security protections, they treat cloud security as a shared responsibility. These vendors relieve significant operational burden from their customers by investing in state-of-the-art security technologies. However, the customer is entirely in control of managing configurations, security updates, and the guest OS, data, and apps. It is therefore important to understand the following best practices to eliminate human-related security threats:
For more information on cloud computing and security, browse the BMC Multi-Cloud Blog or check out these articles: