What Is Hardware Asset Management? Benefits & Lifecycle of a Critical IT Practice


In 1982, Alan Kay famously stated:
“People who are really serious about software should make their own hardware”.
And in this age of cloud and mobile, where we rarely interact with servers and network equipment, it might be easy to think they are no longer as useful as before.
But the hard truth is that good hardware remains the bedrock for all technology services. That’s why having an approach that effectively manages the lifecycle of hardware assets is critical, whether it’s for your own organization or for others, in a hosted arrangement.
Let’s explore hardware asset management and how it works for your organization.
(This article is part of our Sustainable IT Guide. Use the right-hand menu to explore topics related to sustainable technology efforts.)
An asset is any item, thing, or entity that has potential or actual value to an organization. That’s according to ISO.
Value here is about benefits for the organization:
Hardware assets in IT service management refers to assets that are tangible in nature—those you can touch and feel. Hardware assets include those that are in use as well as those in storage.
Some examples of hardware assets, as listed in ITIL® 4, include:
(Explore the related practices of IT asset management and enterprise asset management.)
Hardware assets can be expensive to procure, configure, maintain, and secure. They also require significant management effort and they depreciate rapidly.
Organizations that successfully execute Hardware Asset Management as a discipline often experience enterprise-wide improvements in their operations, and ultimately their bottom lines. These benefits include:
Using automated systems for managing hardware assets, including IoT, can go a long way in raising productivity by:
The same standard defines asset management as the coordinated activity of an organization to realize value from assets.
This coordination covers the acquisition, use, and disposal of assets, as described in the hardware asset management lifecycle from ITAM:
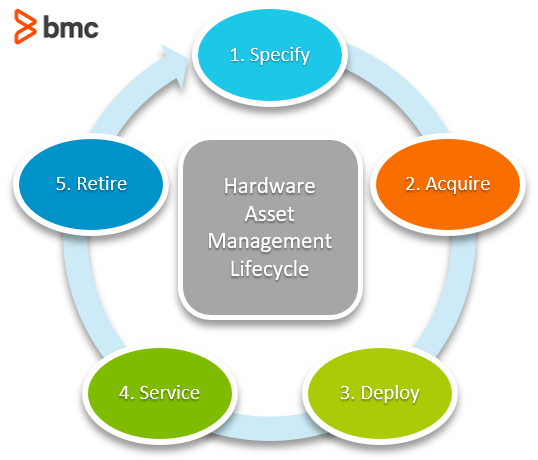 Let’s look at each phase.
Let’s look at each phase.
Hardware planning is usually driven by two perspectives. On the one hand, there is data from business or customer side that is indicative of strategy and demand that influence capacity and type, while on the other hand there are technical aspects driven by evolution, incidents, problems, and continuity factors.
A hardware asset plan will capture these two perspectives, and consolidate the information into a concise approach that meets the priorities of the organization.
Once you’ve identified the priorities, budgeting is the next logical step. Of course, the business plays the bigger role in the decision-making process based on how much funding is available for hardware assets.
Budget will also be determined by preferred acquisition role as upgrades and leasing are considerably cheaper compared to outright purchase.
(See how capital and operating expenses play out over time.)
Following the budget, the procurement process kicks in.
In this phase, you’ll have to write specifications for hardware to a sufficient detail in order to:
Key determinants of which vendors you’ll select usually include:
Procurement will ensure the contract captures elements of support under the service level agreement (SLA).
One alternative to acquisition is to bring your own device (BYOD). In this model, users provide their own computing devices, which will be:
Upon receipt of the hardware assets, your organization must log them in a fixed asset register for financial reasons. This ensures that the financial value from the asset is:
You’ll also tag the asset with the appropriate tagging mechanism, then store the asset in preparation for dispatch and assignment.
The next step, before dispatching and assigning the asset, is to capture the hardware asset as a configuration item
in the relevant IT service management system or register. This supports and device servicing, when necessary, by logging the information needed to support monitoring and maintenance activities by designated IT and vendor support teams.
For end user hardware assets, deployment means either:
For security reasons, you might:
For corporate hardware assets, deployment means:
IT specialists or vendors would conduct these deployment activities. Internal teams, including security specialists and systems audits, then handle the validation process.
At this step, you carry out maintenance of the hardware asset. This usually happens either as:
To support maintenance, an essential activity is spares management, ensuring that faulty parts can be restored quickly and effectively.
Servicing will also include necessary upgrades and patches, which are subject to the existing change management process.
Financial management will track the usage of the asset and compute depreciation as part of annual statutory financial reporting.
Once the hardware asset reaches its useful end of life or is unserviceable, it will then be decommissioned, and then considered for disposal as a logical final step. Decommissioning can also be triggered by:
Decommissioning is a sensitive process when it comes to corporate hardware assets. As such, manage decommissioning using the existing change management processes. Status of the asset should be updated in the IT service management system or hardware asset register.
Before disposal, a security check is required to ensure that the asset is wiped of any corporate information. Specialized techniques might be required to ensure that any data contained in drives is irrecoverable.
Disposal could involve:
Some organizations consider donations to other institutions, e.g. for education or charity.
Finally, update the asset records to reflect the exit of the hardware asset from the organization.
While effective hardware asset management is essential for operational efficiency, cost control, and service quality, there are considerable obstacles. Below are some of the most common challenges companies face.
Hardware asset management isn’t a practice for later. With ramifications around employee productivity, financial health, and overall security, hardware asset management is a critical activity for every organization.